
Teaching Defeat
Chess is the only game where an eight-year-old and a seventy-year-old retiree sit at the same height. In a world that has eliminated waiting, frustration, and defeat, a chessboard can teach what no app can.

Chess is the only game where an eight-year-old and a seventy-year-old retiree sit at the same height. In a world that has eliminated waiting, frustration, and defeat, a chessboard can teach what no app can.

Today's children have never known a world without instant answers. What happens to curiosity when you no longer have to search? A reflection on patience, wonder, and the luxury of not knowing.

AI generates 70% of the code, but it's the remaining 30% — architecture, security, critical thinking — that makes the difference. A reflection on what to study today to build a career in tech, starting from an Amstrad CPC 464 and arriving at AI agents.

How AI agents and the Model Context Protocol are redefining the relationship between humans and software, marking the twilight of the SaaS paradigm and traditional graphical interfaces in favor of conversational interaction based on natural language.

Italy fines Cloudflare €14 million over Piracy Shield. Why blocking IPs and DNS doesn't stop piracy but damages the global architecture of the Internet and digital rights.

A deep dive into the Web Audio API through the lens of building a complete modular synthesizer inspired by the legendary Moog. From oscillators and filters to envelopes and effects, learn how to create professional-grade audio in vanilla JavaScript.

Discover how to extend Laravel’s casting system using CastsAttributes. Learn to transform and manage complex data types seamlessly in your models.
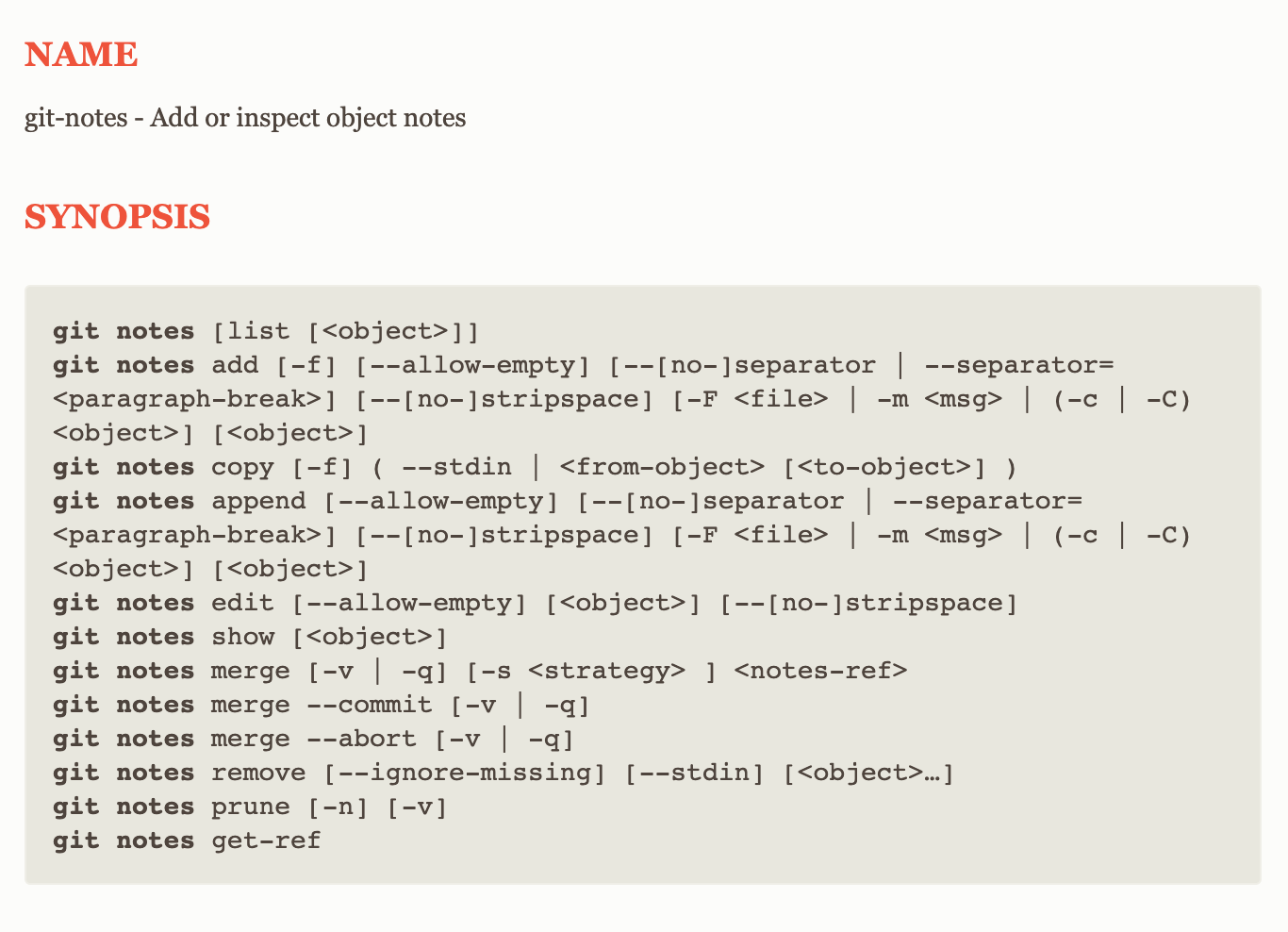
Learn how git notes enables you to add extra information to commits without altering their hashes. Use it to document code reviews, feedback, and annotations directly in your Git history, improving project clarity and collaboration.

MOCA 2024 was an unforgettable weekend, offering a unique platform for knowledge sharing among tech enthusiasts and professionals. With cutting-edge talks ranging from satellite hacking to the application of GenAI models in computer forensics, the event returned to its roots with a focus on innovation and free access to information. Celebrating the 20th anniversary of MOCA and the 30th of Metro Olografix, Italy’s oldest telematics association, the gathering fostered a strong sense of community. My personal highlight was presenting on rapid application development with Laravel and Filament, an incredible experience that made this year’s edition even more special.

I am excited to announce my talk at [#MOCA2024](https://moca.camp). Thanks to Metro Olografix for the opportunity. I will guide you on a journey to show you how to accelerate application development with Laravel and Filament. We will explore how Filament, with its powerful admin interface, seamlessly integrates with Laravel, allowing for the creation of complex applications in a simple and rapid manner. Through practical examples and best practices, we will demonstrate how these technologies can reduce development time and enhance productivity.

A recent update from CrowdStrike inadvertently caused widespread system failures across various Windows systems globally. This incident led to the notorious 'blue screen of death' (BSOD), rendering many systems inoperative, particularly affecting critical infrastructure in airports, hospitals, and financial markets. The faulty driver responsible for the crash was identified, and steps to remedy the situation required manual intervention by system administrators. CrowdStrike quickly responded to the crisis by isolating the issue to a single content update for Windows hosts and deploying a fix. Despite the swift response, the event has sparked discussions on the reliability of endpoint detection and response (EDR) systems and their potential to disrupt the very systems they are meant to protect.
In recent years, NATO has faced escalating cyber threats targeting its critical infrastructure and geopolitical stability. The organization has employed sophisticated strategies, including international cooperation and advanced defense mechanisms, to counter these threats. The necessity for continual enhancement of cyber defenses is emphasized to safeguard the security interests of allied nations.

Laravel 11 introduces the once function, a potent feature designed to optimize application performance by caching the results of expensive operations for the duration of a request. Conceived by Taylor Otwell and Nuno Maduro, once significantly enhances development efficiency, allowing developers to focus on what truly matters. This article delves into the workings of once, its practical applications, and how it can revolutionize the approach to resource management and repetitive operations within Laravel applications.

Laravel 11 marks a significant evolution in the PHP framework's journey, emphasizing streamlined application structures, advanced rate limiting, and robust real-time capabilities through Laravel Reverb. This release sets a new benchmark with enhancements in testing, PHP 8.2 requirement, and seamless integration for developer productivity and application performance.

This article delves into the unconventional use of QEMU for network tunneling, showcasing a sophisticated method that attackers use to infiltrate corporate networks. By examining a specific attack scenario, we emphasize the importance of multi-layered security strategies.
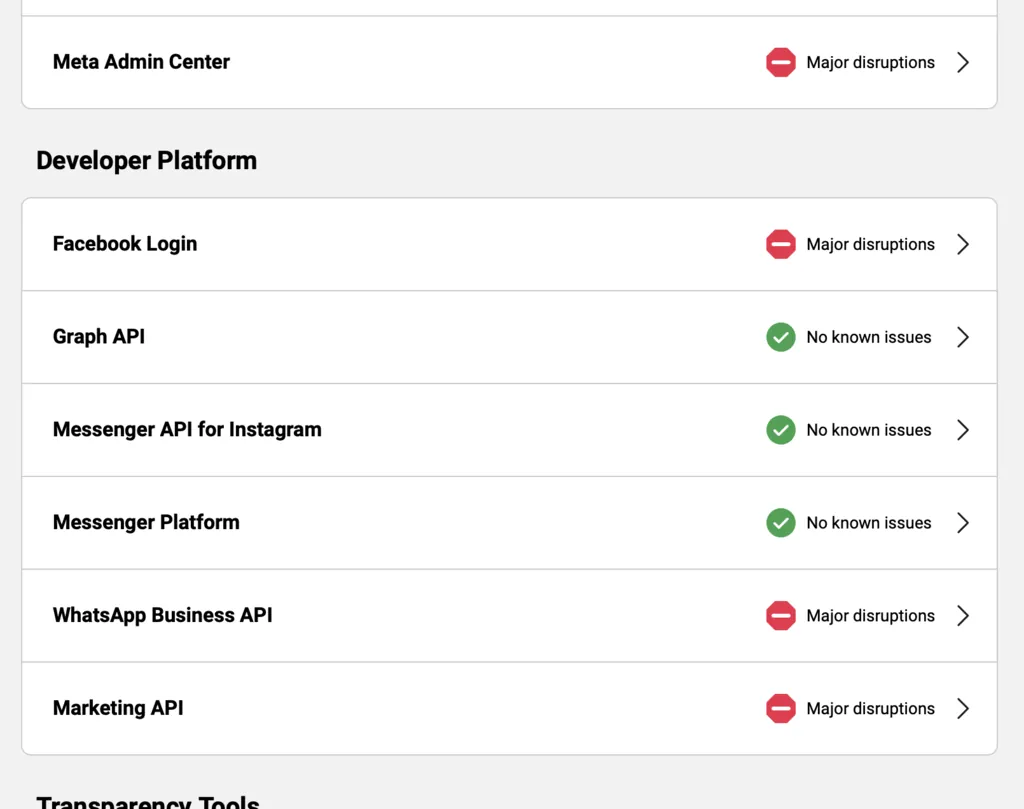
Thousands of users experienced difficulties with Instagram and Facebook on Tuesday afternoon, marking an unexpected outage affecting Meta-owned apps. The issues began to surface around 4 PM Italian time, with reports indicating problems in loading photo feeds, viewing stories, and posting new content. The cause of the disruption remains unclear.

This guide provides a step-by-step approach to customizing user redirection after login within a Laravel application using Jetstream. By implementing a custom LoginResponse class that interfaces with Laravel Fortify, developers can dynamically route users to different dashboards based on their roles, thus improving the user experience and streamlining navigation within the application. The article also covers how to register the custom response and validate the functionality through feature tests using Pest.
The 'Downfall' vulnerability, marked as CVE-2022-40982, highlights a significant security flaw in billions of Intel processors. Originating from memory optimization features, this vulnerability enables malicious users to access and steal sensitive data. Its presence since 2014 underscores the complexities of ensuring digital security in modern tech.
Understanding the official Laravel documentation is crucial for developers, especially beginners. Skipping this vital resource may lead to a lack of comprehension of the framework's full potential and less efficient code. Engaging with the documentation offers numerous benefits, such as comprehensive understanding, best practices, up-to-date information, troubleshooting, and code samples, ultimately resulting in more effective coding practices.
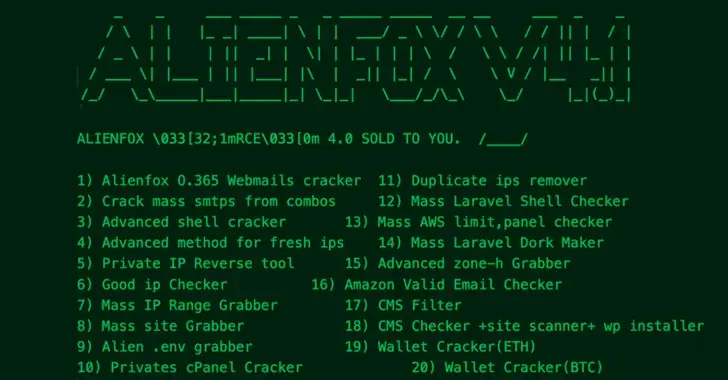
New cybersecurity threat! AlienFox, a highly modular & constantly evolving toolset distributed on Telegram, enables attackers to harvest API keys & secrets from popular cloud service providers like AWS, Google Workspace, and Microsoft 365. AlienFox targets servers associated with popular web frameworks such as Laravel, Drupal, Joomla, Magento, Opencart, Prestashop, and WordPress.
itHub replaced their RSA SSH host key on March 24th to secure Git operations and protect users from potential security risks. The update impacts only Git operations over SSH using RSA, while web traffic and HTTPS Git operations remain unaffected. Users should remove the old key and add the new RSA SSH public key if they encounter a warning message when connecting via SSH. GitHub Actions users may need to update their workflows if they use the ssh-key option